66 percent of organizations would not recover from a cyberattack if it occurred today. Is your organization prepared? Here is what every CIO and CISO needs to know to build or enhance their cybersecurity recovery plan.
Disaster Recovery plans have always been the cornerstone of business continuity. When it comes to protecting your critical assets and avoiding downtime, cybersecurity is an often-overlooked piece of the puzzle, but a critical step in the risk management process.
No matter the size of your business, the cost of a breach could mean the end of your company. In fact, the cost of a data breach is predicted to rise from $3 trillion each year to more than $5 trillion by 2024. This is an average annual growth of 11 percent, reports Juniper Research.
No federal policies, standards or guidelines focus specifically on recovering from a cybersecurity incident. It is up to you to develop, test, and improve your cybersecurity recovery plan for the upcoming year. Use our expertise to help you along the way.
Disaster Recovery is not the same as Cybersecurity Recovery
It is a common misconception that disaster recovery and cybersecurity recovery are one in the same. Although they are similar and have some overlap, disaster recovery’s primary objective is to provide business continuity after disruption from man-made or natural causes. Cybersecurity recovery, on the other hand, protects data assets after a data breach.
“The nature of the threats within security recovery plans are more dynamic than within disaster recovery… for example, recent ransomware attacks, such as WannaCry, are incredibly destructive and require security recovery plans to examine how to effectively respond to new threats and risks,” says Mark Testoni, president and CEO of SAP National Security Services. Most security experts recommend different plans with complementary policies and procedures.
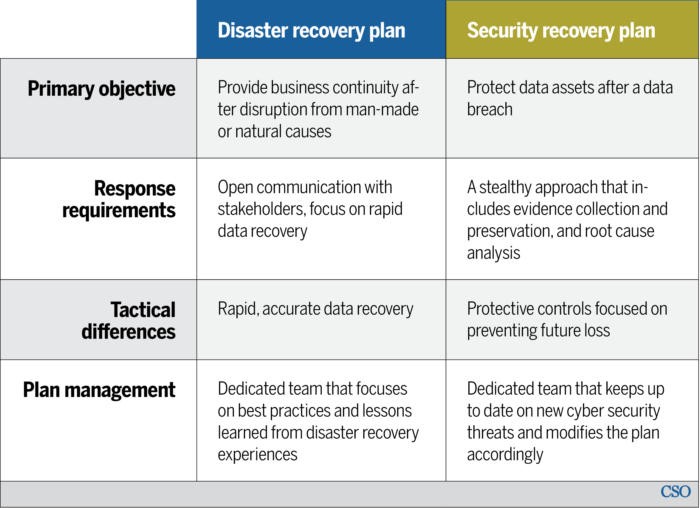
Figure 1: Differences in disaster recovery plan versus security recovery plan (Source: CSOonline.com)
At the end of the day, both plans are part of a larger security objective to ensure the confidentiality, integrity, and availability of your company’s systems and data assets. Disaster recovery directly ties into availability objectives for information security. However, most organizations do not have a true understanding of which elements impact availability.
For instance, most disaster recovery plans start with a secondary location for running data replication between their primary site and secondary disaster recovery site. Consider that a cyberattack may corrupt data, in which case, the disaster recovery implementation will not protect the information since the corrupted data would be replicated to both locations. To avoid this, you should use layered defense tools, and build relevant controls for your risk management process.
Cybersecurity Recovery Objectives
Additional goals for your cybersecurity recovery efforts may include, restoring information systems using alternate methods, performing standard operating procedures in alternate ways, recovering information systems in backup locations, and implementing contingency controls based on the business impact of the incident. When focusing on your cybersecurity response plan, you should follow these steps, and customize each part to your business.
1. Implement Tools and Controls for Layered Protection
As mentioned before, you will also need advanced protection to ensure the success of both your disaster recovery and cybersecurity efforts, such as:
- Preventive elements like a firewall with content inspection and antivirus to block vulnerabilities, exploits, and viruses (plus the address and ports)
- Strict control on changes and software uploads
- Strict access control and audits on activities to prevent compromised data or services
- Applicative firewalling, local anti-virus, and malware protection on business service compute and storage elements
- Timely patch management
Integrity and availability monitoring to detect issues as early as possible
2. Plan for the Recovery Phase
According to Risk Based Security research newly published in the 2019 MidYear QuickView Data Breach Report, the first six months of 2019 have seen more than 3,800 publicly disclosed breaches, exposing an incredible 4.1 billion compromised records.
Businesses of all sizes need to get their security act together, with the business sector accounting for 67 percent of the reported breaches and 84.6 percent of the exposed records according to the report.
While it is preferable to avoid a cyberattack in the first place, the National Institute of Standards and Technology notes that over-reliance on prevention is just as bad as not being prepared. Some cyberattacks simply cannot be stopped, so focusing solely on prevention is a flawed approach. Instead, plan for all possible cyber incidents, their containment and the recovery process. To determine priorities, perform a business impact analysis to evaluate potential effects—financial, legal, regulatory, etc.—of cyber events on your business. With these priorities in mind:
- Define incident management roles and responsibilities
- Develop a Cyber Incident Response Plan and larger Business Continuity Plan with a Crisis Management Strategy
- Make arrangements for communication channels in the event of downtime
- Identify alternate services and/or facilities for your data
- Create and solve “what-if” scenarios based on recent cyber events that have impacted similar organizations
- Identify and fix gaps in crisis planning before an incident occurs
- Consider additional ramifications of a breach including how personnel and stakeholders will be affected and the legal and financial implications of noncompliance
3. Seek Constant Improvement
As you plan for the eventuality of a cyber event, realize the recovery planning process should be fluid. Your organization must update your cybersecurity recovery plan regularly based on up-to-date visibility on threats and risks landscape, best practices, and lessons learned from response to breaches that have affected similar businesses. Consider creating a task force to periodically test and evaluate your recovery efforts and overtime, you will uncover what works and what does not. After a breach, gather your task force and address any vulnerabilities and issues with your plan for more favorable results in the future.
4. Create and Track Recovery Metrics
Rather than simply guessing that the recovery process did or did not work well, use real data and specific metrics to support your position. These suggestions are a great jump-off point when starting from scratch:
- Patch Policy Compliance
- Mean-Time to Patch
- Vulnerability Scan Coverage
- Percent of Systems Without Known Severe Vulnerabilities
- Information Security Budget as % of IT Budget
- Mean-Time to Incident Discovery
- Incident Rate
- Percentage of Incidents Detected
- Mean-Time Between Security Incidents
- Mean-Time to Mitigate Vulnerabilities and Recovery
- Number of Known Vulnerability Instances
- Number of Applications and Percentage of Critical Applications
- Risk Assessment Coverage
- Security Testing Coverage
- Percent of Changes with Security Review
5. Document Everything
Procedures, roles and responsibilities, metrics tracking, and adjustments should be documented for improved response times and recovery. This includes:
- Developing diagrams of infrastructure and equipment
- Maintaining assets and systems inventory, including copies of support agreements with vendors and providers
- Application dependencies and prioritization (restore applications in order of most critical)
- Regulatory compliance information: who, when, and how to contact regulatory bodies and stakeholders in the event of a breach
- Recovery team members and contact information for those employees
With adequate documentation and a comprehensive backup plan, you are more likely to withstand a breach. Think of your cybersecurity recovery plan as a playbook that is shared with your security, business continuity, and contingency planning teams.
Next Steps
Both disaster recovery and a cybersecurity recovery plan are a necessity in today’s cyber risk culture. Data security has become more complex, requiring organizations to invest more resources in issue prevention and remediation.
Having an appropriate well-documented plan spread throughout your departments will maximize your chances of a swift recovery. Practice, training, and metrics will spur continuous improvement that will help your company mitigate risk and thrive despite the growing cyberthreat environment.
LightEdge is committed to keeping our customers’ IT operations, critical applications, and data protected. We provide the technology and resources our customers require to get back to a production state that meets their RTO and RPO requirements.
LightEdge offers a comprehensive set of disaster recovery solutions to ensure uninterrupted performance of IT operations and mission-critical systems in the event of a disaster.
The reliable availability of business IT is essential to the management and livelihood of every company, large or small. All elements hinge on the dependability of your technology to deliver vital information right when you need it.
Redundancy is built into each of our data centers located in Des Moines, Kansas City, Omaha, Austin and Raleigh facilities. Each of our LightEdge facilities strive to deliver more than traditional data centers. We have created true Hybrid Solution Centers designed to offer a complete portfolio of high speed, secure, redundant, local cloud services and managed gateways to public clouds through our hardened facilities.
Want to learn more about LightEdge’s disaster recovery and business continuity services? Contact one of our disaster recovery experts to get started or to schedule your private tour of any of our data center facilities. We have disaster recovery, colocation, and business continuity experts standing by to answer any of your questions.
Related Posts
- What Is Disaster Recovery As A Service (DRaaS)?
- The Best Disaster Recovery Advice For Failover And Failback Success
- Getting Started With Data Protection Planning
- Documentation Is The Key To A Successful Disaster Recovery Plan: Here’s Your Roadmap
- Enterprise Guide to an Effective Disaster Recovery Plan
- How to Make a Business Continuity Plan
- 5 Ways to Prevent Cloud Outages
- The Five Greatest Risks Every Hosting Customer Must Navigate
- Cybersecurity Awareness Month: A Guide to Help Prevent Data Breaches
- Ten Tactics to Protect Against Insider Threats for Cybersecurity
- Ransomware Protection: How to Prevent & Respond to Ransomware Attacks




