Organizations that work with electronic protected health information (ePHI) must carefully weigh the risks and benefits of adopting new technology. From the internet of things (IoT) in hospitals, to wearable medical devices, to bring your own device (BYOD) policies, each endpoint represents a potential network vulnerability.
Avoiding the adoption of new technology is not the answer. In fact, the healthcare sector is predicted to spend nearly $270 billion on IoT devices and services by 2023, reports P&S Market Research. Healthcare is not closing the door on new technology, but instead accepting it with open arms. While, there are risks and consequences, they are not enough to completely avoid the benefits that IoT provides. When adopting this technology, consider the value in education, secure IT solution providers, and security policies to minimize risks.
Enjoy part one of our series on protecting your ePHI in the IoT and BYOD landscape and be sure to look out for part two coming later this week.
IoT in Healthcare: Devices That Transmit ePHI
The term IoT refers to the ability of devices to communicate with one another across internet connectivity, without the need for human intervention. Devices can include sensors, computers, communications devices, and mechanical devices that send and receive data. In the healthcare industry, new devices arrive in the marketplace on a regular basis, such as:
- Patient data-gathering telemetry devices, like wearable heart rate and blood pressure devices
- Connected onsite equipment used for diagnostics, pharmaceutical dosing, and to assist physicians during procedures
- Medical implants (the first wireless pacemaker was implanted in 2009)
According to 2016 projections, analysts expect the market for IoT in healthcare to reach a valuation of $410 billion by 2022. The industry includes the devices themselves, software, hardware, and services.
“Cyber-physical systems could save $63 billion in healthcare costs over 15 years with a 15-30 percent reduction in hospital equipment costs and a 15-20 percent increase in patient throughput,” according to Healthcare IT News
According to Gartner, there will be 20.4 billion IoT devices across all industries by 2020. Data centers will play a major role in information management and harnessing the IoT potential. Gartner reports that about 90 percent of this data will be unstructured, so it will be more important than ever for data centers to continue pushing storage capacity boundaries to keep pace with IoT demands.
In healthcare, IoT will potentially improve response times, diagnostics, and overall health outcomes while saving money and optimizing healthcare workflows. Unfortunately, as the usage of IoT and the development of new tech continues to grow, so does the risk of cyberattacks.
Trends in Healthcare Cybersecurity
A cyberattack of any size can cause severe and permanent damage, particularly for organizations that store, transmit or manage ePHI. Hackers can even potentially use code to take someone’s life. While, to date, no one has reported a medical-device related murder, the possibility exists. In 2015, students at the University of South Alabama successfully simulated a wireless hack and “killed” a patient.
More commonly, attackers use associated devices or access points (i.e., mobile devices, diagnostics equipment, and employee email) to find “back doors” into a facility’s network. From these access points, they can compromise millions or billions of patient records and put healthcare organizations at risk for HIPAA violations. Ransomware, denial of services attacks (DoS) attacks, and other cyber threats are par for the course today.
To put the threat landscape into context, consider the following statistics:
- The 2018 Thales Healthcare Data Threat Report shows the U.S. healthcare has the highest percentage of respondents planning to increase spending for endpoint and mobile device security (62 percent compared with 57 percent global), despite their lack of effectiveness in preventing data breaches.
- The Office for Civil Rights, part of the Department of Health and Human Services (HHS), reported 243 healthcare data breaches in 2016 by mid-October. More than 14.3 million records were taken or exposed by that point in the year.
- Healthcare has been at the top of the list of most frequently attacked industries since 2015.
- The average healthcare organization spent $1.4 million to recover from a cyberattack, according to a recent report from Radware.
- Since late 2015, the Office of Civil Rights collected over $16 million in fines/settlements associated with five organizations involved in ePHI breaches.
A strong cybersecurity strategy reduces the likelihood that an organization will join the list of those breached and in trouble with the Office of Civil Rights
Identifying Vulnerabilities in IoT Devices
“A lot of adversaries aren’t looking at it as ‘let me go and attack your toaster.’ They’re looking at it as ‘let me attack your toaster to use it as a way to get into the rest of your network,’” said President of IP Architects John Pironti.
Something seemingly as innocuous as a smartwatch can create vulnerability if connected to a network housing sensitive data. For organizations that are using multiple personal devices onsite, any connected device represents a vulnerability. Beyond the devices themselves, software and user practices create vulnerabilities.
Sensitive data requires full-time management and monitoring, which is often easier said than done. There are dozens of reasons why your organization can have network vulnerabilities; to simplify the major causes, we divided them into two categories: business and technical. Figure one below outlines the causes of a weak infrastructure, so you can evaluate your own efforts against these factors:
Figure 1: Reasons for IoT Vulnerabilities in Healthcare
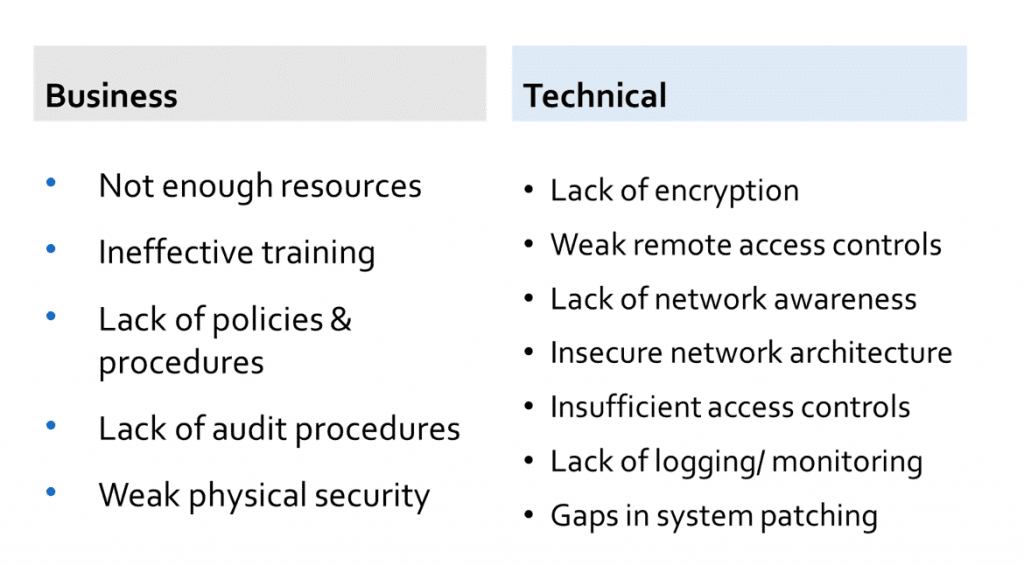
HIPAA regulators outline the basics of healthcare best practices, but do not provide clear standards for software and hardware protections. Every ePHI data handler must take steps to protect their data and manage the risks associated with the IoT to the best of their ability.
Evaluating Connected Devices ePHI in the IoT
Use the following questions to determine the security of each connective device within your network:
- Does the device store and transmit data securely?
- Does it accept software security updates to address new risks?
- Does it provide a new avenue to unauthorized access of data?
- Does it provide a new way to steal data?
- Does it connect to the institution’s existing IT infrastructure in a way that puts data stored there are greater risk?
- Are the APIs that connect the software and devices secure?
Aligning your internal teams, such as C-level leadership, security and IT departments, and any vendors and third-party service providers that touch your network is critical to winning the battle against cybercrime.
Addressing Accountability
Any party that comes into contact with ePHI connectivity may knowingly or unknowingly contribute to vulnerabilities, including insurers, information handling service providers, and healthcare professionals. In many cases, product manufacturers themselves need to take a stronger approach to data privacy and device security.
In addition to regulatory compliance, your organization must develop internal standards for proactive security management, data privacy, and incident response and relay those to any outsiders that affect your network.
Ensure Regulatory Compliance with Our Help
LightEdge has HIPAA secure data center locations at our Des Moines, Kansas City, Omaha, Austin, and Raleigh data center facilities. With LightEdge, you can achieve auditable HIPAA compliance. With a specific background working with healthcare organizations, our data center and hosting solutions provide you with confidence you need to meet HIPAA requirements.
LightEdge offers a free risk assessment from our Chief Security Officer and Chief Compliance Officer as a free resource to all of our customers. Compliance and security are top priorities to guarantee that your data is protected. While there is no certification for HIPAA, LightEdge has successfully undergone a third-party examination against the HIPAA Security Rule and has been issued a Type 1 AT 101 letter of attestation confirming our alignment with HIPAA safeguards. LightEdge is compliant with:
If you are interested in getting a risk-free assessment from our healthcare compliance experts, a tour of any of our HIPAA compliant data centers or to learn more about LightEdge’s compliance offers, contact us here. We have cloud hosting security and compliance experts standing by to answer any of your questions.
For more information on patient privacy and data security, download our free E-book, Patient Privacy and Data Security: Utilizing IT Vendors to Meet HIPAA Compliance and Avoid Risks.
Stay tuned for Part two of our series on protecting your ePHI in the IoT and BYOD landscape, specifically as it relates to cybersecurity. We’ll go further into detail about BYOD and address best practices for policies and control.




